radio-frequency identification card theft While RFID skimming should be the least of your worries, it’s important to take steps to protect against the very real threats of credit card fraud and other forms of identity theft. Be proactive with automatic, 24/7 monitoring of your credit report and credit score, so you’ll . See more $19.45
0 · what is wireless identity theft
1 · what is rfid identification
2 · rfid scam
3 · rfid chip scanning
4 · rfid chip
5 · rfid blocking cards
6 · radio frequency identification
7 · how do rfid cards work
A quick point of clarity to hopefully help you avoid some confusion— the YubiKey NEO was its own series and actually predates the YubiKey 4 series. And yeah technically, but idk how expensive HID NFC readers are. Unless you REALLY .
Radio-Frequency Identification (RFID) involves the use of radio waves to read and capture information stored on an electronic chip attached to an object. RFID chips, or “tags,” can be read via scanning devices from up to several feet away. These chips have been used by businesses for years to manage inventory . See more
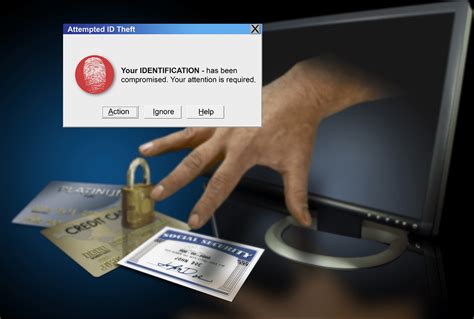
Some security experts have voiced concerns about a phenomenon called RFID skimming, in which a thief with an RFID reader may be able to steal your credit card number or personal information simply by walking within a few feet of you. It’s a scary thought, . See more
While RFID skimming should be the least of your worries, it’s important to take steps to protect against the very real threats of credit card fraud and other forms of identity theft. Be proactive with automatic, 24/7 monitoring of your credit report and credit score, so you’ll . See moreAn industry has sprung up to make wallets and accessories that block hackers from "skimming" data wirelessly through radio frequency identification. But some experts say there's little need.Wireless identity theft is a relatively new technique for gathering individuals' personal information from RF-enabled cards carried on a person in their access control, credit, debit, or government issued identification cards. Each of these cards carry a radio frequency identification chip which responds to certain radio frequencies. When these "tags" come into contact with radio waves, they respond with a slightly altered signal. The response can contain encoded personally identif.
But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you. You may have even seen ads for products like “RFID wallets,” which claim to prevent this kind of theft. An industry has sprung up to make wallets and accessories that block hackers from "skimming" data wirelessly through radio frequency identification. But some experts say there's little need.Wireless identity theft, also known as contactless identity theft or RFID identity theft, is a form of identity theft described as "the act of compromising an individual’s personal identifying information using wireless (radio frequency) mechanics."With the recent shift to contactless payment cards, more cybercriminals are turning to RFID credit card theft via scanning. This article will explain how this theft happens and provide tips on how to protect your RFID credit card from potential thefts and other common payment card frauds.
what is wireless identity theft
Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags. RFID blocking tools claim to protect users against identity theft by stopping criminals from scanning your passport’s ID chip by just rubbing shoulders with you. In practice, however, RFID blocking does little to help in the most likely identity theft scenarios. RFID stands for Radio Frequency Identification. RFID theft occurs when someone uses their own RFID reader to trigger the chip in your credit card; a process called ‘skimming’ or ‘digital pickpocketing.’
what is rfid identification
The encoding process in RFID relies on magnetization in specific patterns that can be picked up when they are unshielded, but many new products use a combination of carbon fiber and aluminum, contained in an appealing case, to . The best way to protect yourself from RFID-related identity theft is by investing in RFID-blocking products like wallets, backpacks, fanny packs, and even pant pockets.
There are a wide variety of attacks that can be performed against RFID access systems. The majority of attacks against RFID systems can be broken into three major categories: man-in-the-middle (MITM), cloning, and brute forcing. But you may have also heard of a scam called RFID skimming, where a thief steals the card number from your chip-embedded card just by walking past you. You may have even seen ads for products like “RFID wallets,” which claim to prevent this kind of theft.
An industry has sprung up to make wallets and accessories that block hackers from "skimming" data wirelessly through radio frequency identification. But some experts say there's little need.Wireless identity theft, also known as contactless identity theft or RFID identity theft, is a form of identity theft described as "the act of compromising an individual’s personal identifying information using wireless (radio frequency) mechanics."With the recent shift to contactless payment cards, more cybercriminals are turning to RFID credit card theft via scanning. This article will explain how this theft happens and provide tips on how to protect your RFID credit card from potential thefts and other common payment card frauds.
Radio Frequency Identification (RFID) tags require a radio signal emitted by the receiver in order to read them. Due to this, they operate within a limited distance and are not capable of transmitting large amounts of data. Examples of RFID tags can be seen in credit cards and door passes. Active Tags. RFID blocking tools claim to protect users against identity theft by stopping criminals from scanning your passport’s ID chip by just rubbing shoulders with you. In practice, however, RFID blocking does little to help in the most likely identity theft scenarios. RFID stands for Radio Frequency Identification. RFID theft occurs when someone uses their own RFID reader to trigger the chip in your credit card; a process called ‘skimming’ or ‘digital pickpocketing.’
The encoding process in RFID relies on magnetization in specific patterns that can be picked up when they are unshielded, but many new products use a combination of carbon fiber and aluminum, contained in an appealing case, to . The best way to protect yourself from RFID-related identity theft is by investing in RFID-blocking products like wallets, backpacks, fanny packs, and even pant pockets.
breath of tge wild nfc card pack
rfid scam
to hacking NFC/RFID Sławomir Jasek [email protected] slawekja Slightly edited version of the slightly edited original photo :) Confidence, Kraków, 4.06.2018 . HF NFC chips built in various readers, e.g. ACR122u USB (~50 EUR). Libnfc: open source library exploiting
radio-frequency identification card theft|rfid chip