can't edit smart card linux To enable smart card authentication we should rely on a module that allows PAM supported . Listen to the LSU Sports Radio Network across the state of Louisiana and .
0 · Smart card authentication with SSH
1 · Smart card authentication
2 · Securing your Ubuntu desktop with Smart Card authentication
3 · Red Hat Enterprise Linux 9
4 · Managing smart card authentication
5 · How to use Smart Card authentication in Ubuntu Desktop
6 · How to Set up SmartCard Authentication on Linux
7 · Chapter 10. Troubleshooting authentication with smart cards
8 · 2FA Linux Smart Card Authentication (PAM + PKCS#11)
$17.99
To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.To enable smart card authentication we should rely on a module that allows PAM supported . It can be used to configure smart card authentication on a Linux system by using the "smartcard" auth provider. And configure PAM (Pluggable Authentication Modules) to use .Overview. In this guide you’ll learn how to configure Smart Card authentication using SSSD as authentication daemon in a way that can be used both for user interface access via GDM login .
If you are having issues authenticating with a smart card, check that you have linked your smart card certificate correctly to a user. By default, a certificate is associated with a user when the .Abstract. With Red Hat Identity Management (IdM), you can store credentials in the form of a private key and a certificate on a smart card. You can then use this smart card instead of .
with-smartcard: Users can authenticate with the user name and password or with their smart card. with-smartcard-required: Users can authenticate with their smart cards, and password .To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 .
Smart card authentication with SSH
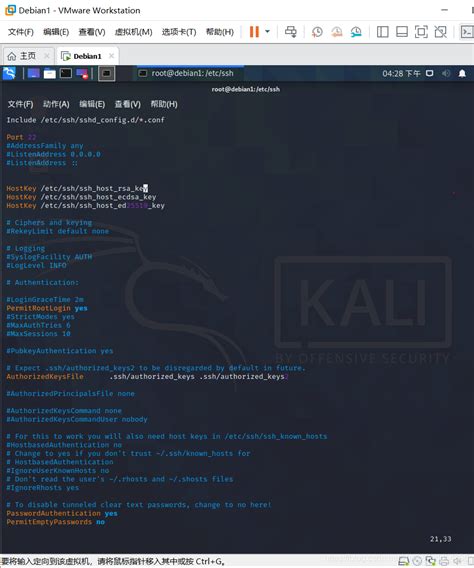
However, the default is ‘yes’. To ensure the setting, edit the sshd_config file and set accordingly. PubkeyAuthentication yes. Restart the SSH server. sudo systemctl restart sshd. Set the public . There are a number of ways to do this, but the following enables smart cards for general authentication. Edit /etc/pam.d/common-auth to include the pam_pkcs11 module: We configure PAM to enforce smart card authentication in addition to the standard password prompt as second factor authentication. You need to have a smart card (with valid .
To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.
It can be used to configure smart card authentication on a Linux system by using the "smartcard" auth provider. And configure PAM (Pluggable Authentication Modules) to use SSSD for smart card authentication.Overview. In this guide you’ll learn how to configure Smart Card authentication using SSSD as authentication daemon in a way that can be used both for user interface access via GDM login and unlock and also some basic principles that are common to headless setups.If you are having issues authenticating with a smart card, check that you have linked your smart card certificate correctly to a user. By default, a certificate is associated with a user when the user entry contains the full certificate as part of the usercertificate attribute.Abstract. With Red Hat Identity Management (IdM), you can store credentials in the form of a private key and a certificate on a smart card. You can then use this smart card instead of passwords to authenticate to services. Administrators can configure mapping rules to reduce the administrative overhead.
with-smartcard: Users can authenticate with the user name and password or with their smart card. with-smartcard-required: Users can authenticate with their smart cards, and password authentication is disabled. You cannot access the system without your smart card.To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need. When a PAM smart card module is enabled, the login process is as follows .However, the default is ‘yes’. To ensure the setting, edit the sshd_config file and set accordingly. PubkeyAuthentication yes. Restart the SSH server. sudo systemctl restart sshd. Set the public key on the server. Extract the user’s public key from the smart card on the SSH client.
There are a number of ways to do this, but the following enables smart cards for general authentication. Edit /etc/pam.d/common-auth to include the pam_pkcs11 module: We configure PAM to enforce smart card authentication in addition to the standard password prompt as second factor authentication. You need to have a smart card (with valid keys) and a PKCS#11 module to read your card (either OpenSC or one from card’s vendor).To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need.
It can be used to configure smart card authentication on a Linux system by using the "smartcard" auth provider. And configure PAM (Pluggable Authentication Modules) to use SSSD for smart card authentication.
Overview. In this guide you’ll learn how to configure Smart Card authentication using SSSD as authentication daemon in a way that can be used both for user interface access via GDM login and unlock and also some basic principles that are common to headless setups.
If you are having issues authenticating with a smart card, check that you have linked your smart card certificate correctly to a user. By default, a certificate is associated with a user when the user entry contains the full certificate as part of the usercertificate attribute.Abstract. With Red Hat Identity Management (IdM), you can store credentials in the form of a private key and a certificate on a smart card. You can then use this smart card instead of passwords to authenticate to services. Administrators can configure mapping rules to reduce the administrative overhead.with-smartcard: Users can authenticate with the user name and password or with their smart card. with-smartcard-required: Users can authenticate with their smart cards, and password authentication is disabled. You cannot access the system without your smart card.
To enable smart card authentication we should rely on a module that allows PAM supported systems to use X.509 certificates to authenticate logins. The module relies on a PKCS#11 library, such as opensc-pkcs11 to access the smart card for the credentials it will need. When a PAM smart card module is enabled, the login process is as follows .However, the default is ‘yes’. To ensure the setting, edit the sshd_config file and set accordingly. PubkeyAuthentication yes. Restart the SSH server. sudo systemctl restart sshd. Set the public key on the server. Extract the user’s public key from the smart card on the SSH client.
Smart card authentication
There are a number of ways to do this, but the following enables smart cards for general authentication. Edit /etc/pam.d/common-auth to include the pam_pkcs11 module:

smart card distribution schedule in mymensingh
Securing your Ubuntu desktop with Smart Card authentication
First, let’s install the react-native-nfc-manager library: npm i --save react-native-nfc-manager Remember to run cd ios && pod install again. Check if the current device has .
can't edit smart card linux|How to Set up SmartCard Authentication on Linux