rfid tags mac address Configure MAC address debugging by entering this command: debug mac addr mac_address. Note. We recommend that you perform the debugging on a per-tag basis. If you enable . An Android NFC app for reading, writing, analyzing, etc. MIFARE Classic RFID tags. - .
0 · Why is using an RFID's unique ID in generating a MAC insecure?
1 · Configuring RFID Tag Tracking
Highlights: https://www.youtube.com/watch?v=n2or4zkoh1kAll rights go to ESPN, ABC, Fox, CBS, NBC, the NFL & its broadcasters. I do not own the music and the .
The primary reason for incorporating the unique ID into the MAC is that it prevents a simple copy of the tag's message and MAC to another tag does not yield a legitimate MAC. .Configure MAC address debugging by entering this command: debug mac addr mac_address. Note. We recommend that you perform the debugging on a per-tag basis. If you enable .
The primary reason for incorporating the unique ID into the MAC is that it prevents a simple copy of the tag's message and MAC to another tag does not yield a legitimate MAC. .Configure MAC address debugging by entering this command: debug mac addr mac_address. Note. We recommend that you perform the debugging on a per-tag basis. If you enable .If the answer to the previous question is “yes,” then is it possible to fetch the MAC address of the reader via coding? —Subham ——— Subham, Tags can be purchased with a unique ID .
See the current configuration for RFID tag tracking by entering this command: show rfid config. Step 2: See detailed information for a specific RFID tag by entering this . All high-frequency cards based on ISO 14443-A standard have a unique chip ID. It acts as the card's serial number, like a network card's MAC address. Usually, the UID is 4 or 7 .Enables RFID tag mobility for specific tags. When you enter the location rfid mobility vendor-name command, tags are unable to obtain a DHCP address for client mode when attempting to .
An important issue in Radio Frequency Identification systems concerns the reading of co-located tags, that must be managed through suitable Medium Access Control (MAC) protocols, .This paper proposes a token-based MAC protocol called Token-MAC for passive RFID systems. Token-MAC is designed to enable fair access to the medium for all tags without requiring a .The RFID tag bears a MAC address unique to the device and an encryption data unit. The tag is readable by a RFID writer/reader to enable a network registration component to obtain the.
MAC Protocols for RFID Systems. Written By. Marco Baldi and Ennio Gambi. Published: 01 February 2010. DOI: 10.5772/7990. IntechOpen. Radio Frequency Identification .

Why is using an RFID's unique ID in generating a MAC insecure?
The primary reason for incorporating the unique ID into the MAC is that it prevents a simple copy of the tag's message and MAC to another tag does not yield a legitimate MAC. .Configure MAC address debugging by entering this command: debug mac addr mac_address. Note. We recommend that you perform the debugging on a per-tag basis. If you enable .If the answer to the previous question is “yes,” then is it possible to fetch the MAC address of the reader via coding? —Subham ——— Subham, Tags can be purchased with a unique ID . See the current configuration for RFID tag tracking by entering this command: show rfid config. Step 2: See detailed information for a specific RFID tag by entering this .
All high-frequency cards based on ISO 14443-A standard have a unique chip ID. It acts as the card's serial number, like a network card's MAC address. Usually, the UID is 4 or 7 .Enables RFID tag mobility for specific tags. When you enter the location rfid mobility vendor-name command, tags are unable to obtain a DHCP address for client mode when attempting to .
An important issue in Radio Frequency Identification systems concerns the reading of co-located tags, that must be managed through suitable Medium Access Control (MAC) protocols, .
This paper proposes a token-based MAC protocol called Token-MAC for passive RFID systems. Token-MAC is designed to enable fair access to the medium for all tags without requiring a .The RFID tag bears a MAC address unique to the device and an encryption data unit. The tag is readable by a RFID writer/reader to enable a network registration component to obtain the.
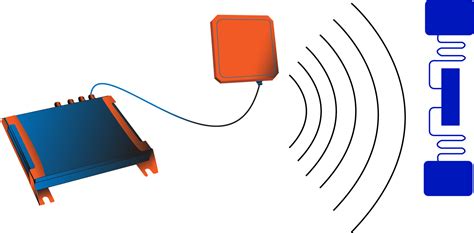
Configuring RFID Tag Tracking
Today’s cards typically use a version of RFID called near-field communication, or NFC, which operates at a higher frequency and allows for faster data transfer, but only at close distances — a few inches.
rfid tags mac address|Configuring RFID Tag Tracking