can rfid transponders be used a tags and readers Active RFID tags have two main types: transponders and beacons. Transponders wait for readers to send a signal before responding, while beacons transmit a signal every .
NFC Reader. NFCard. NDEF Tools For Android. They are outdated, but still try them. Get them on the default F-Droid. NFCGate is actually for assessing NFC traffic, but it's worth playing .
0 · rfid tags for access control
1 · rfid tags and tags
2 · rfid tags and readers
3 · new rfid tags not working
4 · low frequency rfid tags
5 · how to program rfid tags
6 · how rfid tags work
7 · access rfid tags and readers
Saturday, January 2, 1999. 1998 AFC Wild Card Game; Sat 1/2 1 2 3 4 FINAL; Buffalo (10-6): 0: Pass
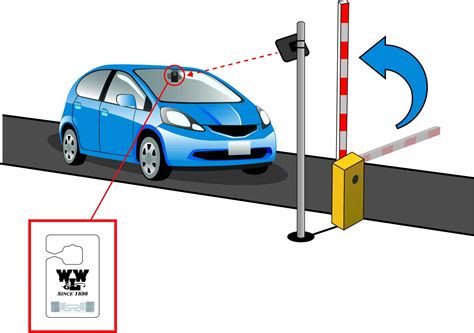
Every RFID solution comprises two main elements: the tags attached to items, and the readers that interrogate those tags. Tags use a chip to store information and can transmit that data via a specific frequency programmed onto the chipset. Readers interpret the radio frequency, read the tag’s data and thus . See moreRFID’s microchip architecture makes it ideal for numerous applications. The cost of the tag ranges from a few cents apiece to several dollars, depending on what items you want to track and what features you need to be included. Ultrahigh-frequency (UHF) . See more
Storing and reading datastarts with an accompanying Electronic Product Code (EPC), which is used as an identifier. Each item receives a . See moreTo discover all the latest innovations and applications for RFID readers and tags, register your attendance at this year’s RFID Journal . See more A tag (or transponder) that returns the signal with information added. The reader usually is connected to a third party system that is accepting (and storing) RFID related events . Active RFID tags have two main types: transponders and beacons. Transponders wait for readers to send a signal before responding, while beacons transmit a signal every .
Two forms of RFID transponder exist. Active tags are battery powered and can be read at a significant distance from the relevant RFID reader. Passive tags are activated .
RFID is similar to other wireless communication technologies such as radio transmitters, Bluetooth, LoRa, etc. Systems are made of two components, tags and readers. Tags contain .
Active RFID tags have two main types: transponders and beacons. Transponders wait for readers to send a signal before responding, while beacons transmit a signal every 3 to 5 seconds. Passive tags do not have a battery and can only send pre-written information to . A tag (or transponder) that returns the signal with information added. The reader usually is connected to a third party system that is accepting (and storing) RFID related events and uses these events to trigger actions. Active RFID tags have two main types: transponders and beacons. Transponders wait for readers to send a signal before responding, while beacons transmit a signal every three to five seconds. Passive tags do not have a battery and can only send pre-written information to .
Two forms of RFID transponder exist. Active tags are battery powered and can be read at a significant distance from the relevant RFID reader. Passive tags are activated (‘energized’) and powered by the electromagnetic energy supplied by the interrogating signal. These will require proximity to the RFID reader to function.RFID is similar to other wireless communication technologies such as radio transmitters, Bluetooth, LoRa, etc. Systems are made of two components, tags and readers. Tags contain data, and readers detect the tag and process the information from the tags when in .
Readers: RFID readers, or interrogators, capture data from RFID tags using antennas to transmit signals, activating nearby tags and receiving transmitted data. They ensure accurate tracking by facilitating communication between tags and the central database.
A common RFID security or privacy concern is that RFID tag data can be read by anyone with a compatible reader. Tags can often be read after an item leaves a store or supply chain. They can also be read without a user's knowledge using unauthorized readers, and if a tag has a unique serial number, it can be associated to a consumer. RF tags use wireless technology. Radio or wireless is a way of transmitting energy through empty space—that is, instead of using a wire cable. The energy is carried by invisible waves of electricity and magnetism that vibrate through the air at the speed of light.
RFID tags can be classified by the radio frequency range they use to communicate (low, high, or ultra-high), and the way the tag communicates with the reader (active or passive). Listed below are the different types of RFID technology, their capabilities and limitations, and the types of applications for which they are best suited. Radio-frequency identification (RFID) technology is used to transfer information wirelessly through radio waves for the purpose of data identification and tracking. It consists of an antenna, transceiver, and transponder (known as either a tag or smart label). An RFID system also requires the appropriate software.
Active RFID tags have two main types: transponders and beacons. Transponders wait for readers to send a signal before responding, while beacons transmit a signal every 3 to 5 seconds. Passive tags do not have a battery and can only send pre-written information to . A tag (or transponder) that returns the signal with information added. The reader usually is connected to a third party system that is accepting (and storing) RFID related events and uses these events to trigger actions.
rfid tags for access control
Active RFID tags have two main types: transponders and beacons. Transponders wait for readers to send a signal before responding, while beacons transmit a signal every three to five seconds. Passive tags do not have a battery and can only send pre-written information to . Two forms of RFID transponder exist. Active tags are battery powered and can be read at a significant distance from the relevant RFID reader. Passive tags are activated (‘energized’) and powered by the electromagnetic energy supplied by the interrogating signal. These will require proximity to the RFID reader to function.RFID is similar to other wireless communication technologies such as radio transmitters, Bluetooth, LoRa, etc. Systems are made of two components, tags and readers. Tags contain data, and readers detect the tag and process the information from the tags when in .Readers: RFID readers, or interrogators, capture data from RFID tags using antennas to transmit signals, activating nearby tags and receiving transmitted data. They ensure accurate tracking by facilitating communication between tags and the central database.
A common RFID security or privacy concern is that RFID tag data can be read by anyone with a compatible reader. Tags can often be read after an item leaves a store or supply chain. They can also be read without a user's knowledge using unauthorized readers, and if a tag has a unique serial number, it can be associated to a consumer. RF tags use wireless technology. Radio or wireless is a way of transmitting energy through empty space—that is, instead of using a wire cable. The energy is carried by invisible waves of electricity and magnetism that vibrate through the air at the speed of light.RFID tags can be classified by the radio frequency range they use to communicate (low, high, or ultra-high), and the way the tag communicates with the reader (active or passive). Listed below are the different types of RFID technology, their capabilities and limitations, and the types of applications for which they are best suited.
bt nfc reader
can an nfc reader read rfid

Reader/writer mode, allowing the NFC device to read and write passive NFC tags and stickers. Card emulation mode, allowing the NFC device itself to act as an NFC card. The .
can rfid transponders be used a tags and readers|rfid tags and readers