information read on silent mode for the rfid system Radio Frequency Identification (RFID) technology uses radio waves to identify . 1 Solution. 05-22-2023 03:52 AM. 1,562 Views. Tomas_Parizek. NXP Employee. Hello, The issue is most probably caused by a noise on the Rx lines -> very high Rx Gain -> The noise generates "60 07 01 a1". The solution would be an .
0 · tuning rfid settings
1 · tuning rfid configuration in session
2 · session 0 rfid
3 · rfid settings explained
4 · rfid session settings
Now, go to home app, create a routine and in the actions select adding your own, then type "Toggle NFC", save the routine and press the button to add it in the home screen (next to delete). Now it just takes the state of the NFC and it just .
In 2007, the Danish Company RFIDsec developed a passive RFID with privacy enhancing technologies built-in including built-in firewall access controls, communication encryption and a . silent mode ensuring that the consumer at point of sales can get exclusive control of the key to . Radio Frequency Identification (RFID) technology uses radio waves to identify .In 2007, the Danish Company RFIDsec developed a passive RFID with privacy enhancing technologies built-in including built-in firewall access controls, communication encryption and a . silent mode ensuring that the consumer at point of sales can get exclusive control of the key to . control the RFID.
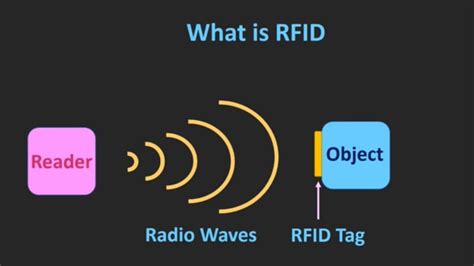
Radio Frequency Identification (RFID) technology uses radio waves to identify virtually anything. It is a wireless system consisting of an RFID tag and an RFID reader. RFID tags store data that can be read, even from a distance-- without making any physical contact or requiring a line of sight.
The process of identifying an asset using RFID involves three main components – the tag itself, a reader or scanner device, and a database or software system for storing and managing data. The first step is encoding information on to each unique tag before attaching it to an asset. With session 2 or 3 after the tags are read, they remain silent for at least two seconds after the reader stops transmitting, allowing other, weaker tags to be heard. Summary The number of RFID configurations can be bewildering, but the following guidelines will get your application going in the right direction: Impinj Protected Mode, a security and privacy feature exclusive to Impinj chips, ensures that a RAIN RFID tag remains silent, making it effectively invisible, unless a reader first provides an 8-character PIN.
All information on RFID tags, such as product attributes, physical dimensions, prices or laundering requirements can be scanned wirelessly by a reader at high speed and from a distance of several metres. Using radio waves, RFID can write, store and transmit information without requiring line-of-sight scanning. Easily reading data from RFID tags allows you to identify single items or entire batches of goods simultaneously.Personal RFID devices – found, e.g., in access cards and contactless credit cards – are vulnerable to unauthorized reading, owner tracking and different types of relay attacks. We observe that accessing a personal RFID device fundamentally requires moving. Guidelines for Securing Radio Frequency Identification (RFID) Systems. Published. April 6, 2007. Author (s) Tom T. Karygiannis, Bernard Eydt, Greg Barber, Lynn Bunn, T. Phillips. Abstract. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks.
RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person.
tuning rfid settings

In 2007, the Danish Company RFIDsec developed a passive RFID with privacy enhancing technologies built-in including built-in firewall access controls, communication encryption and a . silent mode ensuring that the consumer at point of sales can get exclusive control of the key to . control the RFID. Radio Frequency Identification (RFID) technology uses radio waves to identify virtually anything. It is a wireless system consisting of an RFID tag and an RFID reader. RFID tags store data that can be read, even from a distance-- without making any physical contact or requiring a line of sight.
windows 10 require smart card
The process of identifying an asset using RFID involves three main components – the tag itself, a reader or scanner device, and a database or software system for storing and managing data. The first step is encoding information on to each unique tag before attaching it to an asset. With session 2 or 3 after the tags are read, they remain silent for at least two seconds after the reader stops transmitting, allowing other, weaker tags to be heard. Summary The number of RFID configurations can be bewildering, but the following guidelines will get your application going in the right direction: Impinj Protected Mode, a security and privacy feature exclusive to Impinj chips, ensures that a RAIN RFID tag remains silent, making it effectively invisible, unless a reader first provides an 8-character PIN.
All information on RFID tags, such as product attributes, physical dimensions, prices or laundering requirements can be scanned wirelessly by a reader at high speed and from a distance of several metres. Using radio waves, RFID can write, store and transmit information without requiring line-of-sight scanning. Easily reading data from RFID tags allows you to identify single items or entire batches of goods simultaneously.Personal RFID devices – found, e.g., in access cards and contactless credit cards – are vulnerable to unauthorized reading, owner tracking and different types of relay attacks. We observe that accessing a personal RFID device fundamentally requires moving.
tuning rfid configuration in session
Guidelines for Securing Radio Frequency Identification (RFID) Systems. Published. April 6, 2007. Author (s) Tom T. Karygiannis, Bernard Eydt, Greg Barber, Lynn Bunn, T. Phillips. Abstract. This publication seeks to assist organizations in understanding the risks of RFID technology and security measures to mitigate those risks.

session 0 rfid

windows 10 doesnot recognize smart card
windows 10 enable smart card service
NFC Tools – Pro Edition. Price: $3.49. NFC Tools – Pro Edition is an app designed for Android users who want to make the most of NFC technology. This app allows you to read, write, and program tasks on your .NFC Credit Card Emulation. Theoretically, if I had a flipper and used the nfc on the flipper to read a credit card and then saved and emulated the card. Hypothetically could the credit card be used using contact less (theoretically) in stores for small amounts of money and could you actually .
information read on silent mode for the rfid system|tuning rfid settings