smart cards authentication Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and . • Q2 2008 – Testing with employees of transit authorities and select groups of testers.• Q2 2008 – Deployed for users of the RTL only.• Q4 2008 – Deployed for students on all STM, STL and RTL . See more
0 · smart card multi factor authentication
1 · smart card identity
2 · smart card based identification system
3 · smart card authentication step by
4 · smart card authentication protocol
5 · enable smart card log on
6 · enable smart card authentication
7 · authenticate using your smart card
Card Emulation with a Secure Element. When NFC card emulation is provided using a secure element, the card to be emulated is provisioned into the secure element on the device through an Android application. Then, when the user holds the device over an NFC terminal, the NFC controller in the device routes all data from the reader directly to the .
smart card multi factor authentication
How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and . For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture. Smart card subsystem architecture. Credential provider architecture.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.
Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Virtual smart cards offer comparable security benefits to conventional smart cards by using two-factor authentication. The technology also offers more convenience for users and has a lower cost to deploy.
how to create nfc business card
Smart cards, such as debit cards, are often used with a personal identification number (PIN). Organizations also use them for security purposes, as MFA tokens and for authenticating single sign-on users and enabling passwordless authentication. Types of smart cardsSmart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.
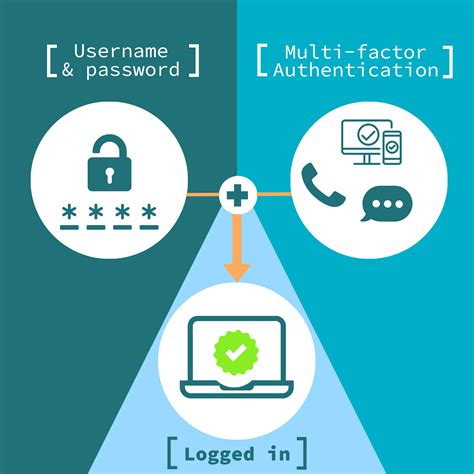
Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server. Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.
For smart cards, Windows supports a provider architecture that meets the secure authentication requirements and is extensible so that you can include custom credential providers. This topic includes information about: Credential provider architecture. Smart card subsystem architecture. Credential provider architecture.How Smart Card Sign-in Works in Windows. This topic for IT professional provides links to resources about the implementation of smart card technologies in the Windows operating system.Smart Card Authentication is a means of verifying users into enterprise resources such as workstations and applications using a physical card in tandem with a smart card reader and software on the workstation. Virtual smart cards offer comparable security benefits to conventional smart cards by using two-factor authentication. The technology also offers more convenience for users and has a lower cost to deploy.
Smart cards, such as debit cards, are often used with a personal identification number (PIN). Organizations also use them for security purposes, as MFA tokens and for authenticating single sign-on users and enabling passwordless authentication. Types of smart cards
Smart card authentication requires two things: the smart card itself and a pin entered by the user. With smart cards there are two different ways to authenticate yourself into a system, there is either contact or contactless smart card readers.
Smart card authentication is a method that employs the embedded chip in the card to verify the identity of the user certificates. The chip can generate or store authentication data through cryptographic algorithms that a reader can verify.Smart card authentication is an important part of cybersecurity, providing an extra layer of protection in our increasingly digital world. It involves the use of smart cards, which are small, pocket-sized cards with embedded integrated circuits or "chips" that can process data.Certificate-based authentication is an encrypted method that enables devices and people to identify themselves to other devices and systems. Two common examples are a smart card or when an employee’s device sends a digital certificate to a network or server.
smart card identity
smart card based identification system
smart card authentication step by

An enabled NFC device can exchange data by using tags and smart posters. A tag can hold a small amount of data that can be read by a device. An enabled NFC device can also write data .As our Android device will act as a real NFC tag, you will need a second NFC-Reader (e.g. a second Android device) to run the tests, because when an Android device is in HCE mode it .
smart cards authentication|authenticate using your smart card