rfid tag modulation This scheme would seem to allow an unlimited number of users to share the electromagnetic spectrum. However, recall that a signal must be modulated in order to convey information. When we modulate the signal, we increase the signal bandwidth. We saw . See more $9.99
0 · rfid modulation techniques
1 · rfid modulation examples
2 · rfid modulation and multiplexing
3 · rfid encoding
4 · rfid coding methods
5 · rfid backscatter equation
6 · ee times rfid modules
7 · backscattering rfid tags
NFC cards support two-way communication, with data exchange between the reader and the NFC card, which makes NFC cards more advantageous in interactive applications. Interaction mode RFID cards usually require the .
Using a single medium for many signals is known as multiplexing. The most common form of multiplexing in radio, in use for almost a century, is frequency-division multiple access (FDMA): different users transmit using different carrier frequencies, and receivers are adapted to capture only the . See moreThis scheme would seem to allow an unlimited number of users to share the electromagnetic spectrum. However, recall that a signal must be modulated in order to convey information. When we modulate the signal, we increase the signal bandwidth. We saw . See moreFinally, the way we code the signal also matters. By examination of Figure 3.6 and Figure 3.8, we can see that pulse interval encoding will result in shorter pulses than OOK for the same . See moreTo clarify why this sort of thing matters in real applications, let’s look at a practical example. In the United States, unlicensed readers randomly . See more
Backscatter is a method of communication in which an RFID tag without a battery (or any internal power source) receives energy from an RFID reader’s transmission and uses that same energy to send back a reply. The . EE Times Explores RFID Modulation, Multiplexing, Pulse Interval Encoding, On-Off Keying, and Practical Applications. Visit To Learn More. Backscatter is a method of communication in which an RFID tag without a battery (or any internal power source) receives energy from an RFID reader’s transmission and uses that same energy to send back a reply. The tag receives the energy via electromagnetic waves propagated from the reader/antenna.The interest in wearable antenna design has increased significantly due to its potential applications for humans, especially in the context of RF identification (RFID) technology. RFID transponders can wirelessly transmit identification numbers or sensor data over short distances.
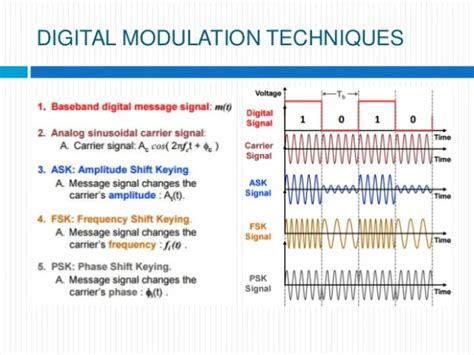
Data exchange between RFID reader and tag can employ various modulation and coding schemes (e. g. amplitude modulation and Manchester coding). The signal transmitted on the forward link (reader to the tag) contains both continuous wave (CW) and modulated commands as shown in Figure 2.The modulation technology used in RFID includes two parts: physical mecha-nism i.e. backscattering modulation and digital modulation technology. 3.1 Backscattering Modulation The de.The tag is composed of an antenna coil and a silicon chip that includes basic modulation circuitry and non-volatile memory. The tag is energized by a time-varying electromagnetic radio frequency (RF) wave that is transmitted by the reader. This RF signal is called a carrier signal.In this paper, a PSK based modulation scheme is proposed in the RFID framework for transmitting at high bit rates from the tag. The PSK modulation circuit is compatible with the existing passive RFID tag RF front end circuit.
The procedures used in RFID systems are the digital modulation procedures amplitude shift keying (ASK), 2 frequency shift keying (2 FSK) and 2 phase shift keying (2 PSK). The use of a modulated subcarrier is widespread in radio technology.To overcome errors in RFID tag return signals, a couple of RF modulation techniques are employed. These include variants of Frequency Shift Keying (FSK) and Phase Shift Keying (PSK) modulation. The variant of FSK that RFID tags typically use involves changing the period of the amplitude-modulated clock cycle.
Modern diodes can operate up to over 1 GHz, allowing passive RFID tags to demodulate a reader signal using only a diode and capacitor. Unmodified OOK is admirably simple and seems promising as a method of modulating areader signal. EE Times Explores RFID Modulation, Multiplexing, Pulse Interval Encoding, On-Off Keying, and Practical Applications. Visit To Learn More. Backscatter is a method of communication in which an RFID tag without a battery (or any internal power source) receives energy from an RFID reader’s transmission and uses that same energy to send back a reply. The tag receives the energy via electromagnetic waves propagated from the reader/antenna.The interest in wearable antenna design has increased significantly due to its potential applications for humans, especially in the context of RF identification (RFID) technology. RFID transponders can wirelessly transmit identification numbers or sensor data over short distances.
Data exchange between RFID reader and tag can employ various modulation and coding schemes (e. g. amplitude modulation and Manchester coding). The signal transmitted on the forward link (reader to the tag) contains both continuous wave (CW) and modulated commands as shown in Figure 2.The modulation technology used in RFID includes two parts: physical mecha-nism i.e. backscattering modulation and digital modulation technology. 3.1 Backscattering Modulation The de.The tag is composed of an antenna coil and a silicon chip that includes basic modulation circuitry and non-volatile memory. The tag is energized by a time-varying electromagnetic radio frequency (RF) wave that is transmitted by the reader. This RF signal is called a carrier signal.
In this paper, a PSK based modulation scheme is proposed in the RFID framework for transmitting at high bit rates from the tag. The PSK modulation circuit is compatible with the existing passive RFID tag RF front end circuit.The procedures used in RFID systems are the digital modulation procedures amplitude shift keying (ASK), 2 frequency shift keying (2 FSK) and 2 phase shift keying (2 PSK). The use of a modulated subcarrier is widespread in radio technology.To overcome errors in RFID tag return signals, a couple of RF modulation techniques are employed. These include variants of Frequency Shift Keying (FSK) and Phase Shift Keying (PSK) modulation. The variant of FSK that RFID tags typically use involves changing the period of the amplitude-modulated clock cycle.
can i request a non rfid credit card
rfid modulation techniques
rfid modulation examples
rfid modulation and multiplexing

The nfc trigger is found in events as a "NFC Tag". I'm no expert in credit cards nfc chips, but I found this in r/nfc. I dont think you could cut tha card smaller and keep the nfc. I would recommend you to get some nfc stickers or tags. Propably 22 .
rfid tag modulation|rfid encoding