rfid reader theory In this paper, the author introduces the principles of RFID, discusses its primary technologies and applications, and reviews the challenges organizations will face in deploying this technology. Published in: IEEE Pervasive Computing ( Volume: 5 , Issue: 1 , Jan.-March 2006 ) NFC is the technology in contactless cards, and the most common use of NFC technology in your smartphone is making easy payments with Samsung Pay. NFC can also be used to quickly connect with wireless devices and transfer .
0 · what is rfid technology
1 · what is a rfid system
2 · rfid research topics
3 · rfid research paper
4 · rfid reader function
5 · rfid journal articles
6 · introduction to rfid
7 · examples of rfid research
iOS 11.0+ iPadOS 11.0+ Mac Catalyst 13.1+ protocol NFCReaderSessionProtocol. .
There are two types of RFID readers -- fixed readers and mobile readers. The RFID reader is a network-connected device that can be portable or permanently attached. It uses radio waves to transmit signals that activate the tag. Once activated, the tag sends a wave back to the .
In this paper, the author introduces the principles of RFID, discusses its primary .
An RFID (Radio Frequency Identification) reader is a device that uses radio .
There are two types of RFID readers -- fixed readers and mobile readers. The RFID reader is a network-connected device that can be portable or permanently attached. It uses radio waves to transmit signals that activate the tag.
In this paper, the author introduces the principles of RFID, discusses its primary technologies and applications, and reviews the challenges organizations will face in deploying this technology. Published in: IEEE Pervasive Computing ( Volume: 5 , Issue: 1 , Jan.-March 2006 )
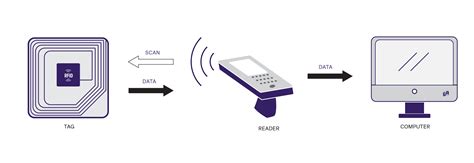
Discover how RFID readers work and revolutionize industries with their ability to track and identify objects using radio waves. Explore the applications and benefits of this innovative technology. However, a basic RFID system is not that complex; it is made of three important components: (i) a tag, which can be embedded in or attached to a physical product to be tracked and traced; (ii) a reader and its antennas, which interact with the tag without requiring a line of sight; and (iii) a host computer or middleware, which is in charge of .Rather than using light to collect or read a number from a bar code, radio waves are used to read a number from the RFID tag. RFID therefore does not need line-of-sight to operate. RFID technology increases efficiency and accuracy in carrying out daily activities, especially in the business field.
RFID is a technology similar in theory to bar codes. However, the RFID tag does not have to be scanned directly, nor does it require line-of-sight to a reader. The RFID tag it must be within the range of an RFID reader, which ranges from 3 to 300 feet, in order to be read.RFID extends the reach of supply chain information systems in such a way that it will soon be possible and economically feasible to tag valuable physical objects and then to track and trace them, enabling many novel and useful applications. In this survey, we make an exhaustive review of RFID technology working towards connecting all the physical devices to the internet.
This paper provides a survey on radio frequency identification (RFID) technology. Initially RFID tags were developed to eventually replace barcodes in supply chains.There are two types of RFID readers -- fixed readers and mobile readers. The RFID reader is a network-connected device that can be portable or permanently attached. It uses radio waves to transmit signals that activate the tag. In this paper, the author introduces the principles of RFID, discusses its primary technologies and applications, and reviews the challenges organizations will face in deploying this technology. Published in: IEEE Pervasive Computing ( Volume: 5 , Issue: 1 , Jan.-March 2006 ) Discover how RFID readers work and revolutionize industries with their ability to track and identify objects using radio waves. Explore the applications and benefits of this innovative technology.
However, a basic RFID system is not that complex; it is made of three important components: (i) a tag, which can be embedded in or attached to a physical product to be tracked and traced; (ii) a reader and its antennas, which interact with the tag without requiring a line of sight; and (iii) a host computer or middleware, which is in charge of .
tnepds smart card download
Rather than using light to collect or read a number from a bar code, radio waves are used to read a number from the RFID tag. RFID therefore does not need line-of-sight to operate.
RFID technology increases efficiency and accuracy in carrying out daily activities, especially in the business field. RFID is a technology similar in theory to bar codes. However, the RFID tag does not have to be scanned directly, nor does it require line-of-sight to a reader. The RFID tag it must be within the range of an RFID reader, which ranges from 3 to 300 feet, in order to be read.
what is rfid technology
RFID extends the reach of supply chain information systems in such a way that it will soon be possible and economically feasible to tag valuable physical objects and then to track and trace them, enabling many novel and useful applications. In this survey, we make an exhaustive review of RFID technology working towards connecting all the physical devices to the internet.
what is a rfid system
rfid research topics
Data cross-checks across Visual zone, MRZ, barcode, RFID. Get an ideal image with advanced document capture capabilities. Regula Document Reader SDK technology improves ID verification results with image preprocessing .Once you have installed the package, you can import it and calliing one of the readPassport(:) functions available in NFCPassportReader class is enaugh to start an NFC read of the travel document.. You can pass the document .
rfid reader theory|introduction to rfid